This guide will provide you with ideas about how to use VirusTotal. Threat Hunters, Cybersecurity Analysts and Security Engineers, you are all welcome!
The guide is designed to give you a comprehensive overview into VirusTotal by providing all the basic information about how it works and out-of-the-box examples to help you in different scenarios, such as how to:
- Ingest Threat Intelligence data from VirusTotal into my current architecture.
- Monitor phishing campaigns impersonating my organization, assets, intellectual property, infrastructure or brand.
- Get further context to incidents by exploring relationships and mapping out a threat campaign.
- Understand which vulnerabilities are being currently exploited by attackers, what kind of malware they are distributing and what actors are behind.
Get the most out of VirusTotal
Advanced search engine over VirusTotal's dataset, with richer details and context about threats. Allows you to download files for further study and dissection offline. Tell me more.
Leverage YARA's advanced rule-crafting capabilities for files, urls, domains, and IPs. Hunt live threats, analyze campaign evolution, and identify hidden indicators of compromise with exceptional precision. Tell me more.
Explore VirusTotal's dataset visually and discover threat commonalities. Understand the relationship between files, URLs, domains, IP addresses and other observables encountered in an ongoing investigation. Tell me more.
The VirusTotal API lets you upload and scan files or URLs, access finished scan reports and make automatic comments and much more without the need of using the website interface. In other words, it allows you to build simple scripts to access the information generated by VirusTotal. > Tell me more.



Tailored training to provide you and your team with the essential knowledge and skills for effective investigation and contextualization of malicious activities.
Here are some of the main use cases our existing customers undertake in VirusTotal, this is not a comprehensive list, but some great ideas.
Anti-phishing, anti-fraud and brand monitoring
Discovering phishing campaigns impersonating your organization.
Automatic security telemetry enrichment
Threat intelligence is as good as the data it ingests
Incident response and Forensic analysis
Pivot, discover and visualize the whole picture of the attack
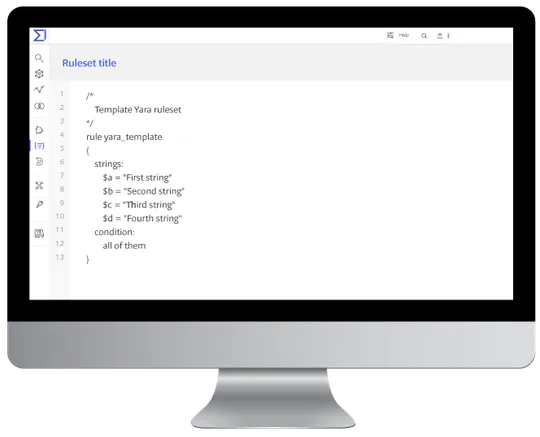
YARA is a multi-platform program running on Windows, Linux and Mac OS X that can be used to search for malware within VirusTotal. You may want to do this in order to:
- Gain insight into phishing and malware attacks that could impact your organization.
- Discover emerging threats and the latest technical and deceptive attack techniques.
- Spot fraud in-the-wild, identify network infrastructure used to steal credentials and take measures to mitigate ongoing attacks.
- Track the evolution of known bad actors that have targeted your organization in the past and stay ahead of them.
In general, YARA can help you proactively hunt for threats live no matter where they begin to show up. This is something that any company can do, no matter what sector they operate in to make sure that they are protected.
You can think of it as a programming language that’s essentially just for rules to match and recognize malware. You can find all its documentation at YARA's documentation.
VirusTotal was born as a collaborative service to promote the exchange of information and strengthen security on the internet. The initial idea was very basic: anyone could send a suspicious file and in return receive a report with multiple antivirus scanner results. In exchange, antivirus companies received new malware samples to improve protections for their users. Thanks to the collaboration of antivirus companies and the support of an amazing community VirusTotal became an ecosystem where everyone contributes and everyone benefits, working together to improve internet security.
You can find out more information about our policy in the following links:
Below you can find additional resources to keep learning what else can you get from VirusTotal